Adsotech's SAP Role Management Initiative - What We Have Noticed So Far
- Adsotech

- May 27, 2025
- 3 min read
Espoo, Finland - 28.05.2025. Role Management, Role Design and governance are a headache for IT and security teams. Having to constantly fulfill requests for new roles, checking for SoD conflicts, manually developing best practices and fixing recurring issues makes it tempting to just outsource the whole thing, and many have.

Our involvement in SAP Role Management has come about quite incidentally. As a software and services provider in the SAP ecosystem, we've observed that significant bottlenecks in Role Management can create knock-on effects and delays when deploying our solutions. To us, this signals broader issues at play — and a challenge that extends beyond simply accelerating deployment.
Nevertheless, we get to hear more and more compelling cases for more efficient, holistic and transparent role design and management on a weekly basis as we keep digging deeper.
Here is what we have Noticed so far:
Role Management, Role Design is Often Manual, Time Consuming & Rigid
Users are asked what transactions they need through emails and meetings and through a series of guesses, trials and errors. Users often end-up with too little or too much access.
SoD conflicts and access issues creep into the system. Once transactions are included in roles, they’re set in stone, even if a user might only need that specific transaction occasionally. The occasional user might have more access than intended, and issues arise because of this.
Click to see how our solution from Pathlock solves these problems
Role design is automated and based on real usage data - No guesswork, meetings, back and forth emails or downtime required.
RBAC + ABAC approach - Users can be granted access to transactions in a dynamic, data centric manner
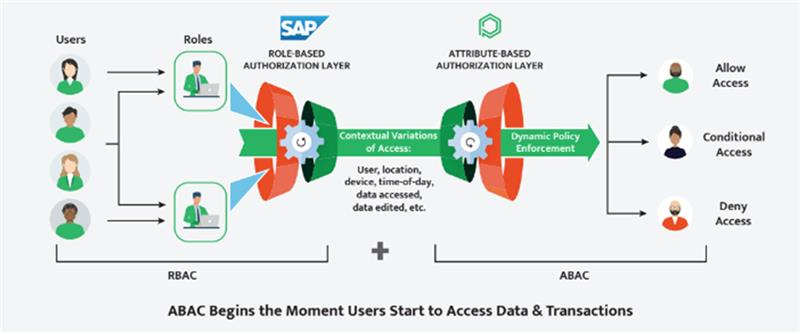
SoD Conflicts do Occur, if Roles are Not Simulated Before deployment
The Role Design process rarely involves simulations, which leaves SoD risk and access analysis insufficient. If and when problems occur, they’re unexpected and resolving them require undue amounts of time that in most cases could be better spent elsewhere.
Click to see how our solution from Pathlock solves these problems
All roles are tested for issues using simulations and 'What-if' type analysis before they're deployed.
Roles are subject to consistent documentation over their lifecycle - Role documentation is supported and made available for security teams. This lets the security team respond efficiently to incidents or future design requests.
AI - powered Remediation helps analyze risks and gives guided recommendations.
There is a sense of a lack of control over roles, changes, visibility
Maintaining, changing and governing roles is often a scattered and disintegrated process. Most times there is no central repository for roles, which makes day-to-day problem solving and building sensible governance structures challenging. Poor and scattered visibility over the roles, their structure and usage data makes it hard to know what problem areas exist before they manifest themselves. Roles multiply and diverge without a sustainable role lifecycle management model, which keeps adding to the problem.
Click to see how our solution from Pathlock solves these problems
Role Management offers a centralized repository that allows admins to compare roles to each other and leverage model roles to accelerate their work.
Role Management facilitates troubleshooting roles in production by helping security teams understand why a role exists, why it was designed the way it was, and how it was tested.
Changes between ECC and S/4HANA create challenges in access management
Transferring roles from ECC to S/4HANA is not a simple task. There are many changes between the two versions, e.g, one of the more prevalent ones is the new BP transaction replacing customer and vendor transactions. Mapping access, transferring roles and checking for old SoD conflicts is hard in a cross app, multi-platform environment.
The new setup is intended to simplify and remove redundancies from systems, but what this often does is creates confusion with users and exposes errors in internal controls due to users not knowing what they can/cannot or should/shouldn’t do. Also, SAP’s yearly simplification document is a hassle to implement and keep up with.
Click to see how our solution from Pathlock solves these problems
SAP's yearly simplification document and changes are automatically integrated into the solution. No need to read through or decipher anything.
Pathlock's Role Management Module identifies obsolete transactions and replaces them with mapping to new Business Partner transactions.
We keep learning more and more as discussions progress and what we take away from these discussion is increasingly fascinating. We at Adsotech would love to hear more views about Role Management, SoD and Role Design and general SAP security.
Our lines are open, so do not hesitate to contact us if the issues described in this text resonate or you wish to share your views about Role Management.
.png)



Comments